Back to the MAC
(With link to tomorrow mornings meeting at 7am Brisbane time and tomorrow night's show on Cafe locked out 7pm Sunday night Brisbane time also)
Hi guys,
Our usual Sunday morning meeting is on as always for paid subscribers, and I’m looking forward to continuing the deep-dive discussions with everyone.
This week, I’ve been re-focusing on MAC addresses — specifically where we're at with them in 2025 and what patterns are still holding. While revisiting some of the work I did with Mateo Taylor back in 2022/23, I came across something worth flagging: an unregistered MAC address that I observed repeatedly over a full 12-month period starting November ‘22.
It stood out for two reasons — it started with 44 and ended in DD, making it easy to track, and it broadcasted an extremely stable signal the entire time. No manufacturer assignment. No shifts. Just a persistent, identifiable presence.
Under standard protocols, MAC addresses should be assigned to a registered manufacturer block. This one wasn’t — or at least not in any of the public registries we cross-checked at the time.
The consistency and coherence of the signal are what make this especially unusual. Across multiple dates and locations, the signal strength remained stable, ranging between -93 dBm and -79 dBm over the course of more than a year. Such a consistent and prolonged signal suggests something more structured and persistent than casual device emissions.
Mateo and I nicknamed this device 'The 44-DD Phantom' and continued tracking it during scans. While many unidentified MACs appeared and disappeared, this one remained consistent. Its repeated presence and stable signal strength pointed to a source operating in a predictable and structured manner.
Observed Patterns and Anomalies
When comparing MAC address datasets from 2022 and 2025, several notable patterns emerged:
100% OUI Turnover: Every MAC address detected in 2025 was unregistered and unmatched to the 2022 dataset. This suggests a complete replacement of identifiers or a shift to a new broadcasting regime that bypasses conventional attribution systems.
Entropy Compression: The MAC addresses detected in 2025 displayed a compressed entropy range, clustering around a narrow band of values. This uniformity indicates a potentially programmatic or engineered generation process.
Persistent Signals Across Time and Location: Despite environmental variability, certain unregistered MACs, including ‘44 double D’ as she was affectionately referred to - appeared consistently over time. This points to a stable, structured broadcasting mechanism rather than random, incidental signals.
These findings suggest that standard commercial Bluetooth hardware may not account for all observed signals. I’ve started referring to this pattern as Synthetic Emission Architecture (SEA), which encompasses signals that may not adhere to traditional device identification protocols.
Additionally, BLE scanner logs show that some unknown MACs are consistently associated with 2000 ms intervals — a detail worth investigating further. While this doesn’t directly explain 44 double D, it suggests there could be a broader structural pattern at play.
New Observations with nRF Software
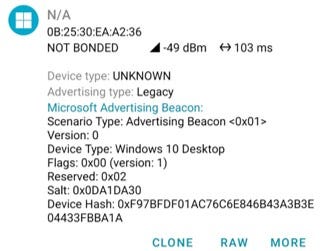
I've also been trialling new scanning software from nRF, developed by Nordic Semiconductor, which has a strong presence in Internet of Bodies (IoB) technology and holds significant shareholding from the Norwegian government. Interestingly, their software attributes all unregistered MAC addresses that start with a letter to Google. This simplistic attribution model raises questions about the metadata being read from these unregistered MAC addresses. This particular one has a first number < 4 and is attributed to Microsoft. The attribution rules are not completely figured out but I’m working on it…
The fact that MAC addresses starting with 8 or 9 are excluded or filtered out is also notable. Such an omission is inconsistent with expectations of randomized MAC generation, which should include all hexadecimal digits (0-9, A-F).
The attribution rules applied by the nRF software appear to be overly simplistic or potentially guided by predefined metadata categories. This could be worth exploring further to understand how these unregistered addresses are being classified.
I'll be diving deeper into these findings during my talk on Café Locked Out tonight at 8 pm Sydney time.
👉 Rumble Link: Back to the MAC - Café Locked Out 7pm Brisbane time Sunday night
Would love to hear everyone’s thoughts on this. See you at the meeting in the morning or at the show tonight!
I hope the rest of the weekend goes well.
Cheers
David
PS Thanks for the ongoing support! - all coffees gratefully received!
www.drdavidnixon.com
Keep reading with a 7-day free trial
Subscribe to Nixonlab to keep reading this post and get 7 days of free access to the full post archives.